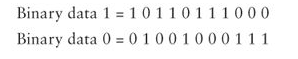Coding
. . . .
Coding
- RF signals can get altered or corrupted in many ways.
- Because 802.11 uses an unbounded medium with a huge potential for RF interference, it had to be designed to be resilient enough that data corruption could be minimized.
- To achieve this, each bit of data is encoded and transmitted as multiple bits of data.
- The task of adding additional, redundant information to the data is known as processing gain.
- In this day and age of data compression, it seems strange that we would use a technology that adds data to our transmission, but by doing so, the communication is more resistant to data corruption.
- The system converts the 1 bit of data into a series of bits that are referred to as chips. To create the chips, a Boolean XOR is performed on the data bit and a fixed-length bit sequence pseudorandom number (PN) code.
- Using a PN code known as the Barker code, the binary data 1 and 0 are represented by the following chip sequences:
- This sequence of chips is then spread across a wider frequency space.
- Although 1 bit of data might need only 2 MHz of frequency space, the 11 chips will require 22 MHz of frequency carrier space.
- This process of converting a single data bit into a sequence is often called spreading or chipping.
- The receiving radio converts, or de-spreads, the chip sequence back into a single data bit.
- When the data is converted to multiple chips and some of the chips are not received properly, the radio will still be able to interpret the data by looking at the chips that were received properly.
- When the Barker code is used, as many as 9 of the 11 chips can be corrupted, yet the receiving radio will still be able to interpret the sequence and convert them back into a single data bit.
- This chipping process also makes the communication less likely to be affected by intersymbol interference because it uses more bandwidth.
- After the Barker code is applied to data, a series of 11 bits, referred to as chips, represent the original single bit of data.
- This series of encoded bits makes up 1 bit of data.
- To help prevent confusion, it is best to think of and refer to the encoded bits as chips. The Barker code uses an 11-chip PN; however, the length of the code is irrelevant.
- To help provide the faster speeds of HR-DSSS, another more complex code, Complementary Code Keying (CCK), is utilized. CCK uses an 8-chip PN, along with using different PNs for different bit sequences.
- CCK can encode 4 bits of data with 8 chips (5.5 Mbps) and can encode 8 bits of data with 8 chips (11 Mbps).
Reference:
Coleman, David D.,Westcott, David A. CWNA: Certified Wireless Network Administrator Official Study Guide: Exam CWNA-106 Wiley.
Coleman, David D.,Westcott, David A. CWNA: Certified Wireless Network Administrator Official Study Guide: Exam CWNA-106 Wiley.
|
|