Layer 2 and Layer 3 roaming
. . . .
Layer 2 and Layer 3 roaming
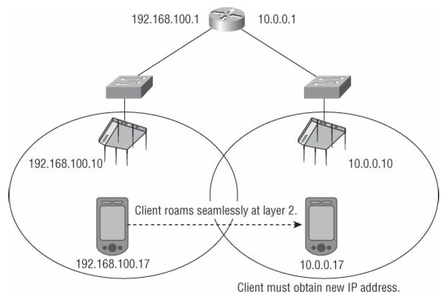
Layer 2 roaming
802.11k
802.11r
Layer 3 roaming
Layer 2 roaming
- One of the most common issues you’ll need to troubleshoot is problems with roaming.
- Roaming problems are usually caused by poor network design or faulty client
device drivers. - Client stations, and not the access point, make the decision on whether or not to roam between access points.
- Some vendors may involve the access point or WLAN controller in the roaming decision, but ultimately, the client station initiates the roaming process with a reassociation request frame.
- The method by which a client station decides to roam is a set of proprietary rules determined by the manufacturer of the 802.11 radio, usually defined by receive signal strength indicator (RSSI) thresholds.
- RSSI thresholds usually involve signal strength, noise level, and bit-error rate.
- As the client station communicates on the network, it continues to look for other access points via probing and listening on other channels and will hear received signals from other APs.
- The variable of most importance will always be received signal strength: As the received signal from the original AP grows weaker and a station hears a stronger signal from another known access point, the station will initiate the roaming process.
- However, other variables such as SNR, error rates, and retransmissions may also have a part in the roaming decision.
- When roaming, a client sends a frame, called the reassociation request frame, to start the roaming procedure.
- Because roaming is proprietary, a specific vendor client station may roam sooner than a second vendor client station as they move through various coverage cells.
- Some vendors like to encourage roaming, whereas others trigger roaming at lower received signal thresholds.
- The best way to ensure that seamless roaming will commence is proper design and a thorough site survey.
- When you’re designing an 802.11 WLAN, most vendors recommend 15 percent to 30 percent overlap of –70 dBm coverage cells.
- Too little duplicate coverage will effectively create a roaming dead zone, and connectivity might even temporarily be lost.
- On the flip side, too much duplicate coverage will also cause roaming problems.
- If a client station can also hear dozens of APs on the same channel with very strong signals, a degradation in performance will occur due to medium contention overhead.
- Another design issue of great importance is latency. The 802.11-2012 standard suggests the use of an 802.1X/EAP security solution in an enterprise.
- The average time involved during the authentication process can be 700 milliseconds or longer.
- Every time a client station roams to a new access point, reauthentication is required when an 802.1X/EAP security solution has been deployed. The time delay that is a result of the authentication process can cause serious interruptions with time-sensitive applications.
- VoWiFi requires a roaming handoff of 150 milliseconds or much less when roaming. A fast secure roaming (FSR) solution is needed if 802.1X/EAP security and time-sensitive applications are used together in a wireless network.
- Currently, most WLAN vendors implement a nonstandard method of FSR called opportunistic key caching (OKC) that has grown over the years in terms of client-side support.
- The IEEE has defined fast basic service set transition (FT) mechanisms as a standard for fast and secure roaming; however, widespread support on the client side for FT mechanisms has yet to become a reality.
- Now that the Wi-Fi Alliance has implemented the Voice Enterprise certification, standardized FT mechanisms are slowly becoming a reality.
- Changes in the WLAN environment can also cause roaming problems.
- RF interference will always affect the performance of a wireless network and can make roaming problematic as well.
802.11k
- The ratified 802.11k amendment defined the use of radio resource measurement (RRM) and neighbor reports to enhance roaming performance.
802.11r
- The ratified 802.11r amendment also defines faster secure handoffs when roaming occurs between cells in a wireless LAN using the strong security defined in a robust security network (RSN).
- Most WLAN infrastructure vendors already support 802.11k and 802.11r technology in their APs and controllers, but most client devices do not.
- Some aspects of the 802.11r (secure roaming) and 802.11k (resource management) amendments are tested by the Wi-Fi Alliance with a certification called Voice Enterprise.
- Although the Voice Enterprise certification is a reality, the majority of clients still do not support 802.11k and 802.11r mechanisms.
Layer 3 roaming
- Wi-Fi operates at layer 2 and roaming is essentially a layer 2 process.
- When the client roams and reestablishes, layer 3 connectivity will have to be restarted.
- The only way to maintain upper-layer communications when crossing layer 3 subnets is to provide a layer 3 roaming solution that is based on the Mobile IP standard.
- Mobile IP is an Internet Engineering Task Force (IETF) standard protocol that allows mobile device users to move from one layer 3 network to another while maintaining their original IP address.
- Mobile IP is defined in IETF request for comment (RFC) 3344. Layer 3 roaming solutions based on Mobile IP use some type of tunneling method and IP header encapsulation to allow packets to traverse between separate layer 3 domains with the goal of maintaining upper-layer communications. Most WLAN vendors now support some type of layer 3 roaming solution.
- Mobile client receives an IP address, also known as a home address, on a home network.
- The mobile client’s IP address is known to a device on the network called the home agent (HA). The original WLAN controller on the client’s home network serves as the home
agent. - The home agent is a single point of contact for a client when it roams across layer 3 boundaries. The HA shares client MAC/IP database information in a table called a home agent table (HAT) with another device called a foreign agent (FA). In this example, the foreign agent is another WLAN controller that handles all Mobile IP communications with the home agent on behalf of the client. The foreign agent’s IP address is known as the care-of address.
- When the client roams across layer 3 boundaries, the client is roaming to a foreign network where the FA resides.
- The FA uses the HAT tables to locate the HA of the mobile client station.
- The FA contacts the HA and sets up a Mobile IP tunnel.
- Any traffic that is sent to the client’s home address is intercepted by the HA and sent through the Mobile IP tunnel to the FA.
- The FA then delivers the tunneled traffic to the client and the client is able to maintain connectivity using the original home address.
- Mobile IP tunnels are established between access points if the WLAN vendor does not use controllers.
Reference:
Coleman, David D.,Westcott, David A. CWNA: Certified Wireless Network Administrator Official Study Guide: Exam CWNA-106 Wiley.
Coleman, David D.,Westcott, David A. CWNA: Certified Wireless Network Administrator Official Study Guide: Exam CWNA-106 Wiley.
|
|